· Eduardo Vieira · Critical · 2 min read
Zero Trust & IEC 62443: The New Rules of Engagement for OT Security
The air gap is a myth. Here is how to secure your connected factory using the IEC 62443 framework and Zero Trust principles.
In the last year, ransomware attacks on industrial targets increased by 87%. The attackers aren’t hacking PLCs directly; they are phishing an HR employee, jumping to the OT network via a flat VPN, and encrypting the SCADA server.
If your security strategy relies solely on a firewall at the edge, you are already compromised.
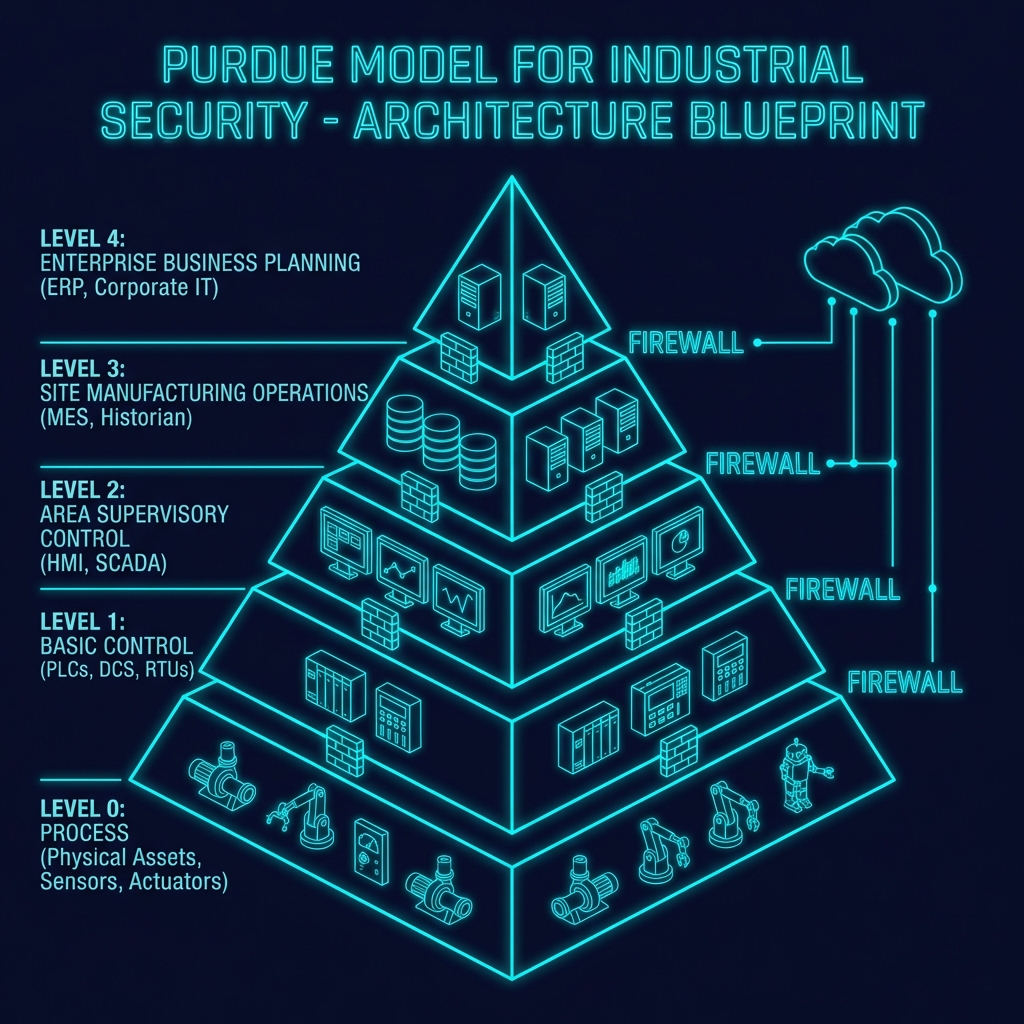
The Evolution of the Purdue Model
The traditional Purdue Model (isolating levels 0-5) is evolving. With IIoT, sensors (Level 0) talk to Cloud (Level 5). We don’t abandon Purdue; we reinforce it with Zero Trust.
Zero Trust in OT means:
- Verify Explicitly: Authenticate every connection. No “trusted IPs.”
- Least Privilege: A maintenance tech only gets access to the specific HMI they need, not the whole subnet.
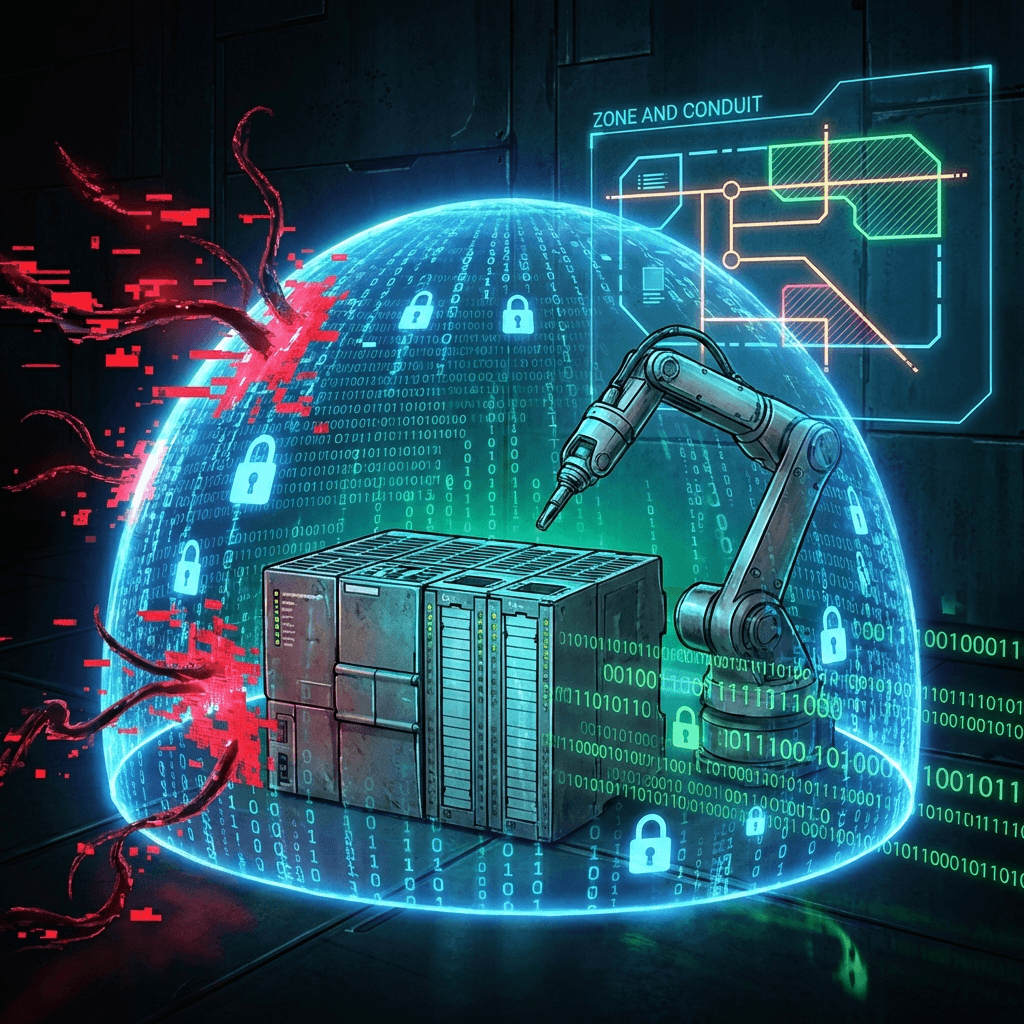
- Assume Breach: Design your network so that if the HMI is compromised, the PLC is still safe.
IEC 62443: The Bible
We align all architectures with IEC 62443-3-3.
- Zones & Conduits: Group assets with similar security requirements (e.g., “Packaging Zone”) and police the “conduits” between them with industrial firewalls.
- MFA: Mandatory for any remote access. No exceptions.
- Patch Management: Yes, you have to patch Windows. But do it after validating on a staging environment.
Practical Steps for 2026
- Network Segmentation: Kill the “flat network”. Use VLANs and ACLs.
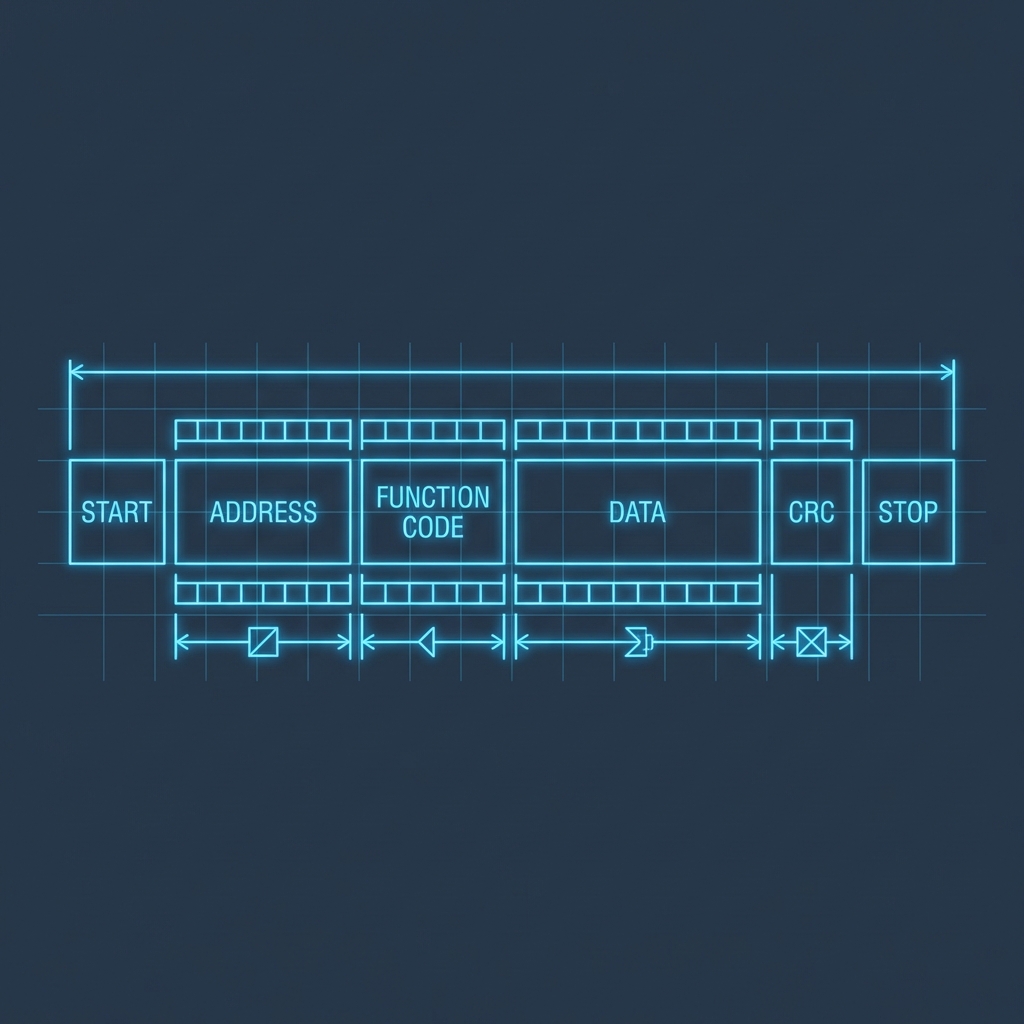
- Deep Packet Inspection (DPI): Your firewall should know the difference between a Modbus
Read(Safe) and a ModbusWrite(Dangerous). - Continuous Monitoring: Use tools like Nozomi or Claroty to passively listen to traffic and detect anomalies (e.g., a PLC being reprogrammed at 3 AM).
Secure Your Legacy
Security is not a product; it’s a process. Don’t wait for a ransom note to take this seriously.
I help plants conduct IEC 62443 audits and implement defense-in-depth architectures. Secure your operations.