· Eduardo Vieira · Industrial Connectivity · 2 min read
Connecting Siemens S7-1500 PLCs to the Cloud: OPC UA & Latency Guide
Forget inefficient polling. Learn to use OPC UA Subscriptions, security certificates, and asynchronous Python to send plant data to the cloud robustly.
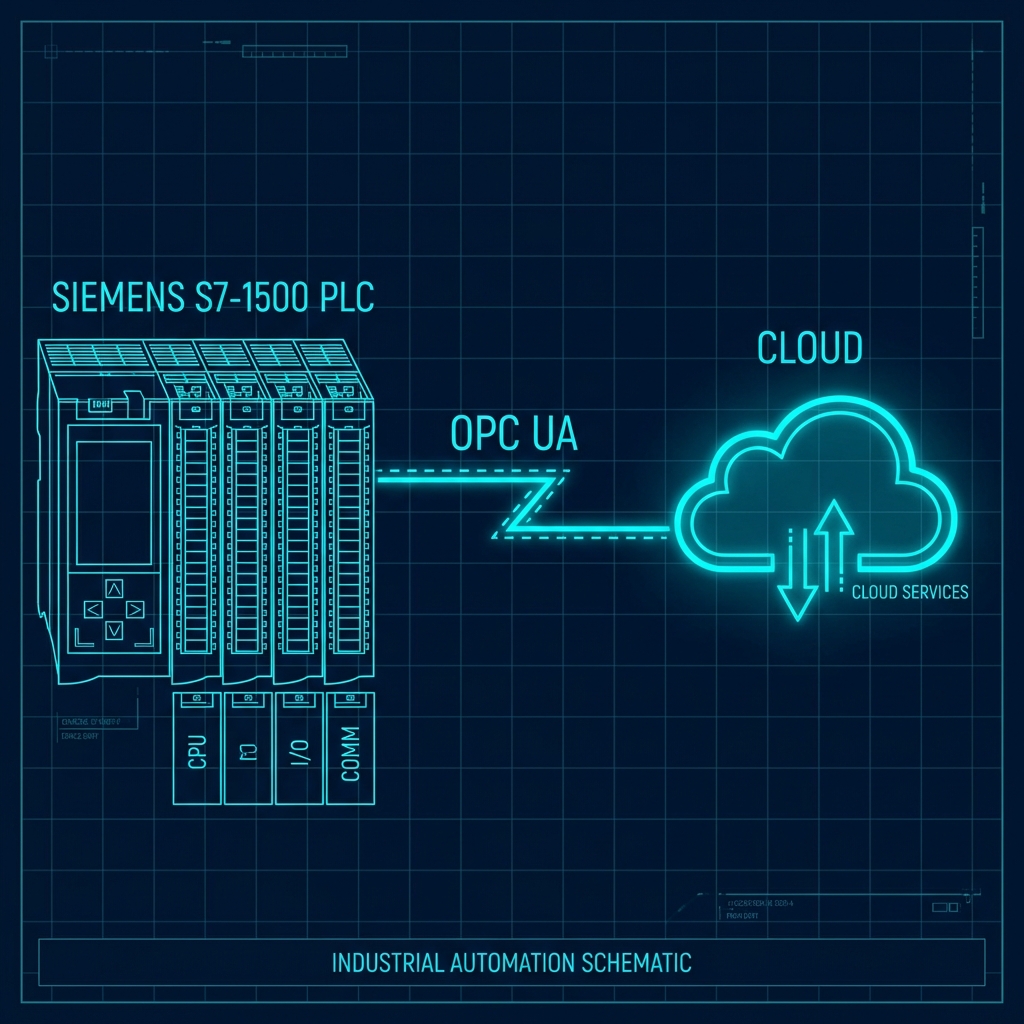
Sending data from a Siemens S7-1200 or S7-1500 PLC to the cloud (AWS, Azure, or a remote SCADA) is one of the most common tasks today. But doing it “quick and dirty” with constant polling saturates the PLC’s scan cycle and generates unpredictable latencies.
Modern industry uses OPC UA (Unified Architecture). In this guide, I’ll show you how to build a professional Gateway using asynchronous Python and why you should use Subscriptions instead of Reads.
1. The Polling Mistake: Why is my PLC hanging?
Traditional polling (asking “do you have the data?” every 100ms) consumes PLC CPU even if the value hasn’t changed. If you have 1000 tags, your network will collapse.
The Solution: OPC UA Subscriptions. With subscriptions, the client (your gateway) tells the server (the PLC): “Notify me only when the value changes more than 1% (Deadband) or when it changes state”. The PLC manages this internally and pushes the data to the gateway only when necessary.
2. Configuration in TIA Portal
For this to work, you must first enable the server in the PLC:
- CPU Properties: General -> OPC UA -> Server -> [x] Enable Server.
- Security: Enable certificate-based authentication. Do not expose your PLC without a password; it is industrial suicide.
- Tags: Make sure the DBs (Data Blocks) have the “Accessible from OPC UA” checkbox checked.
3. Asynchronous Gateway with Python
I have developed a production template that you can use as a base. It uses opcua-asyncio to handle hundreds of tags without blocking the main thread.
👉 Repository: siemens-cloud-gateway
Subscription Logic Example
async with Client(url="opc.tcp://192.168.0.1:4840") as client:
handler = MySubscriptionHandler()
sub = await client.create_subscription(500, handler)
# Subscribe to a tag in a specific DB
node = await client.get_node("ns=3;s=\"DB_Global\".\"MotorSpeed\"")
await sub.subscribe_data_change(node)4. Latency and Jitter: What to expect?
In an industrial local network (Profinet/Ethernet), you can expect:
- PLC to Gateway: 5-20ms.
- Gateway to Cloud: 50-200ms (depending on region).
If you need ultra-low latency (< 10ms) for closed-loop control, OPC UA is not for sending to the cloud; it’s for inter-cell communication or a local Edge Gateway.
Conclusion
Connecting an S7-1500 to the cloud securely requires understanding OPC UA certificates and optimizing traffic with subscriptions. Using a Docker container-based architecture (like the one in my repo) allows you to scale the solution to multiple production lines in minutes.
Technical Sources:
- Siemens Support: Configuring OPC UA on S7-1500
- OPC Foundation: OPC UA Specifications Overview
- GitHub: opcua-asyncio Library Docs